Krebsonsecurity hits with a recent record of 6.3 TBPS DDOS – Krebs

Last week Krebsonsecurity suffered a nearly-record distributed services (DDOS) attack that exceeded 6.3 data at 6.3 times per second (terabit is a trillion bits of data). The brief attack appears to be a test run for large-scale new Internet of Things (IoT) botnets, capable of launching severe digital attacks that few network destinations can afford. Keep reading for more about botnets, attacks, and the obvious creators of this global threat.
For reference, last week’s 6.3 TBP attack was ten times the size of the assault launched against the site in 2016 in 2016 Mirai IoT Botnet, keep Krebsonsecurity offline for nearly four days. The attacks in 2016 were so big that akamai – Pro-DDOS protection for Krebsonscurity was being provided at the time – asked me to leave the service because the attack was causing problems for their paid customers.
Krebsonsecurity.com has been a protection since Mirai attack Project Shielda free DDOS defense service Google Subsidiaries puzzle Provides websites that provide news, human rights and election-related content. Google Security Engineer Damian Menscher Tell Crabson to safely, the May 12 attack is the largest Google processing ever. Second only to very similar attacks in terms of pure scale Cloudflare Reduced and written in April.
After comparing notes with Cloudflare, Menscher said that both botnets that launch attacks have fingerprints AisuluThis is a digital siege that first surfaced less than a year ago. Menshe said the attack on Crabson security lasted less than a minute, throwing large UDP packets on random ports Speed of approximately 585 million packets per second.
“This is the type of attack that is usually designed to overwhelm the network link,” Menscher said. “For most companies, an attack of this size kills them.”
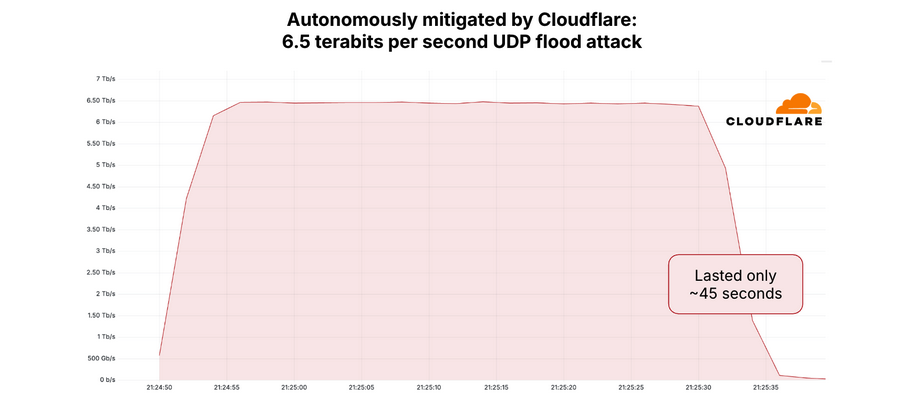
Graphics depicting CloudFlare mitigated 6.5 TBP attacks in April 2025. Image: Cloudflare.
The Aisuru botnet includes a globally scattered collection of invasive IoT devices, including routers, digital video recorders and other systems commanded through default passwords or software vulnerabilities. As the researchers Qianxin XLABthe botnet was confirmed for the first time in August 2024 in an attack on a large gaming platform.
According to reports, Aisulu became quiet after contact until it reappeared in November, with more firepower and software vulnerabilities. In a January 2025 report, Xlab discovered new and improved Aisuru (aka “Airashi”) In the CNPILOT router, previously unknown zero-day vulnerabilities have been incorporated.
Don’t wander around
The people behind Aisuru Botnet have been publicly peddling their DDOS machines telegraph A chat channel closely monitored by multiple security companies. In August 2024, the botnet was rented at a subscription tier ranging from $150 a day to $600 a week, offering up to two Terabits attacks per second.
“You may not attack any measurement wall, health care facility, school or government site,” Aisuru Botnet owner posted on a telegram in August 2024.
Interested parties are told to contact the telegram handle”@yfork“Purchase a subscription. Account @yfork used a nickname before”Sepia,” has been posting identity to the DDOS-centric Telegram channel since 2021.
According to the FBI, the DDOS rental area of the stalemate has been occupied in several law enforcement operations over the years. Last year, Forky said in a telegram that he was selling the domain name Pressure device[.]The bestThis is the server caught by the FBI in 2022, part of an ongoing international law enforcement effort aimed at reducing the supply and demand for DDOS hiring services.
The FBI’s FBI Seizure Warrants (PDF) issued by the FBI reads, “The operator of this service calls itself ‘borky'[.]The best. The FBI warrant states that on the same day the seizure was announced, Forky posted a link to the story on this blog detailing the operation of the domain name seizure, adding: “We are now buying our new territory.”
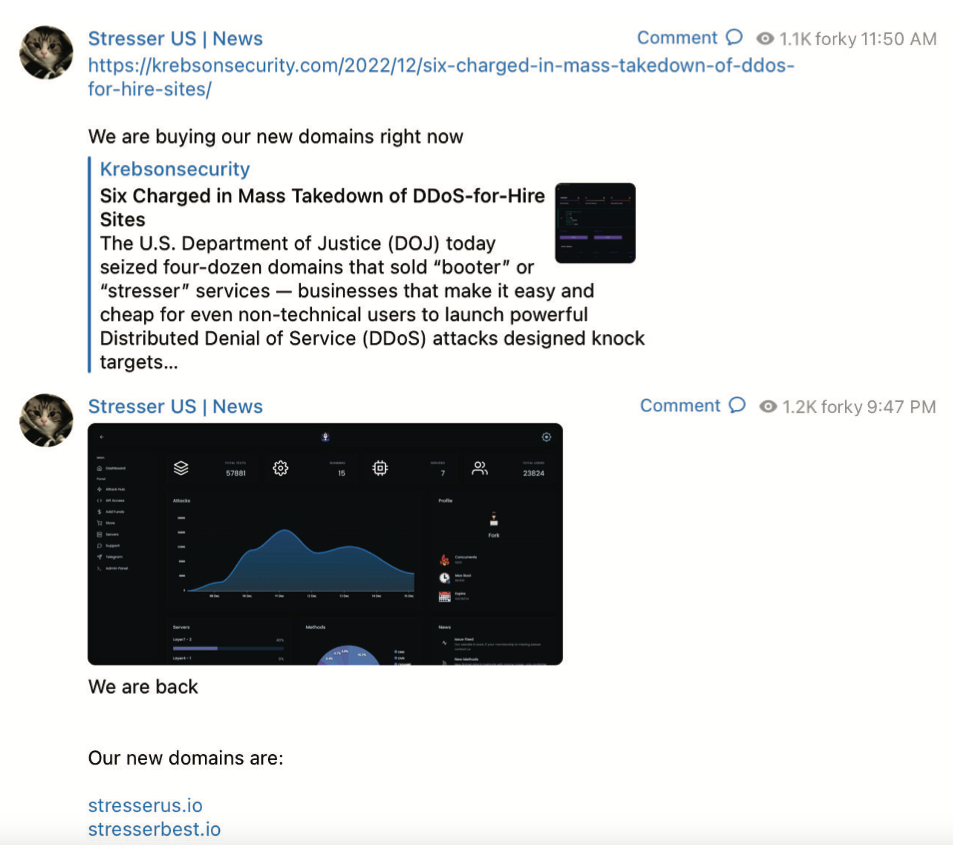
Screenshots of the FBI seizure order for Forky’s DDOS-For-For-For-for-for domain, show that Borky announced the resurrection of their services in the new domain.
About ten hours later, Forky released again, including screenshots of the pressure symbol[.]Best user dashboard, instructing customers to use their saved password on a new website.
Cyber Intelligence Inc. Indexes “The Lockdown” review of public telegram channel posts Unit 221b and Flash point – Revealed a 21-year-old man who claims to live in Brazil [full disclosure: Flashpoint is currently an advertiser on this blog].
Borky’s posts have often promoted the DDOS mitigation companies and ISPs he runs since the second half of 2022 Botshield[.]io. The Botshield website connects to a commercial entity registered in the UK called Botshield Ltd, which lists a 21-year-old woman from Sao Paulo, Brazil as director. Internet routing records indicate that Botshield (AS213613) currently controls hundreds of internet addresses allocated to companies earlier this year.
Domaintools.com Report Botshield[.]IO was registered in July 2022 Kaike Southier Leite in St. Paul. The LinkedIn profile of the same name says the person is a Brazilian network expert who works in “planning and implementing a strong network infrastructure with a focus on security, reducing DDOS, hosting, hosting and cloud server services.”
Meet fluffy

Image: jaclyn vernace / shutterstock.com.
In his public telegram chat channel posts, Forky has hardly tried to cover up his whereabouts or identity. In numerous chat conversations indexed by Unit 221B, forky can be seen talking about Brazil’s daily life, often talking about Brazil’s extremely low or high prices in a range of goods (from computers and networking devices to narcotics and food).
Forky touched through Telegram, claiming he has “had not been involved in this illegal operation for many years” and that the project has been taken over by other unspecified developers. Forky initially told Krebsonsecurity that he had left the botnet scene for years, only when he made a public post from the telegram late last year, it wasn’t true.
Forky denied being involved in the attack on Krebsonsecurity, but admitted that he helped develop and market Aisuru Botnet. Forky claims he is now just a staff member of the Aisu Botnet team and he stopped the botnet about two months ago after starting a family. Falki also said the woman, known as the director of Botsilder, was associated with him.
Forky responded ambiguously to many questions about Aisuru Botnet and its business efforts. But once he knew very well:
“I have zero fears about you, the FBI or Interpol,” Forky said, asserting that he is now almost entirely focused on their hosting business—Botshield.
Forky declined to discuss the composition of its ISP customers or clarify whether Botshield is more of a hosting provider or DDOS mitigation company. However, Forky posted information on the telegram about Botshield’s successful mitigation of large DDOS attacks launched against other DDOS hiring services.
Domaintools found the same Sao Paulo street address in Botshield’s registration record[.]IO is used to register several other domains, including Can’t be reduced[.]us. The email address in the WHOIS record of the domain is [email protected], which Domaintools says is used to register the domain name of the domain name Pressure device[.]usone of the domains occupied by the FBI’s 2023 crackdown.
May 8, 2023, U.S. Department of Justice Announcement to seize the pressure[.]We, as well as more than a dozen other areas that provide DDOS services. The Justice Department said 10 of these 13 areas were reincarnations of the service caught in a previous scan in December, targeting 48 top-tier stress servers (also known as “boots”).
Forky claims he can find out who attacked my website with Aisuru. But a day later, Forky said he would return empty-handed.
“I tried to ask, all the big guys don’t have enough mental retardants to attack you,” Forky explained in a telegram interview. “I have nothing to do with it. But you are welcome to write this story and try to blame me.”
Mirai’s Ghost
Last week’s 6.3 TBP attack did not significantly damage the site, partly because it was so brief – lasting about 45 seconds. This scale and concise DDOS attack is often generated when a botnet operator wants to test or prove that its firepower is in the interest of potential buyers. Indeed, Google’s Menscher said last month’s May 12 attack on Cloudflare and the slightly larger 6.5 TBP attack may just test the capabilities of the same botnet.
In many ways, the threat posed by Aisuru/Airashi Botnet is reminiscent of Mirai, an innovative IoT malware strain that emerged in the summer of 2016 and successfully surpassed all other IoT malware strains that were available at the time.
As Krebsonsecurity first revealed in January 2017, Mirai’s author is two American men who share DDOS mitigation services—even if they sell more lucrative DDOS hire services using the most powerful Botnet on the planet.
Less than a week after using the Mirai botnet to target Crabson security in a days-long DDO, the Mirai authors posted the source code to their botnet, so if federal investigators were arrested, they would not be the only ones who owned it.
Ironically, the leak from the Mirai source is exactly what led to the Mirai authors’ final reveal and arrest, who continued to serve their sentences, demanding that they be subject to probation, asking them to consult FBI investigators about the DDOS investigation. However, this leak also quickly led to the creation of dozens of Mirai botnet clones, many of which were to promote their own powerful DDOS hiring services.
Menscher told Krebsonsecurity that although it may sound counterintuitive, the internet might be better if Aisuru’s source code becomes public knowledge. After all, the people behind Aisulu have been continually competing with other IoT botnet operators, all working to direct a limited number of vulnerable IoT devices worldwide, he said.
He said this development would almost certainly lead to the spread of Aisuru botnet clones, but at least in this way, the overall firepower of each plant network will be greatly reduced — or at least within the mitigation capabilities of most DDOS protection providers.
Menscher said it would be nice if someone posted a full list of software exploits used by Aisuru operators, unless the source code leaked.
“Part of the reason Mirai is so dangerous is that it effectively eliminates competitive botnets,” he said. “This attack somehow managed to compromise all these boxes that others don’t know about. Ideally, we would like to see those scattered [individual botnet operator] Too much control. ”



