Danabot malware developer infects his own PC -Krebs on Serivica
Today, the U.S. government filed criminal charges against 16 people accused of operating and selling DanabotSince 2018, it has sold prolific information propaganda malware on Russian cybercrime forums. FBI The new version of Danabot was used for espionage, and many defendants exposed their real-life identity after accidentally infected their system.
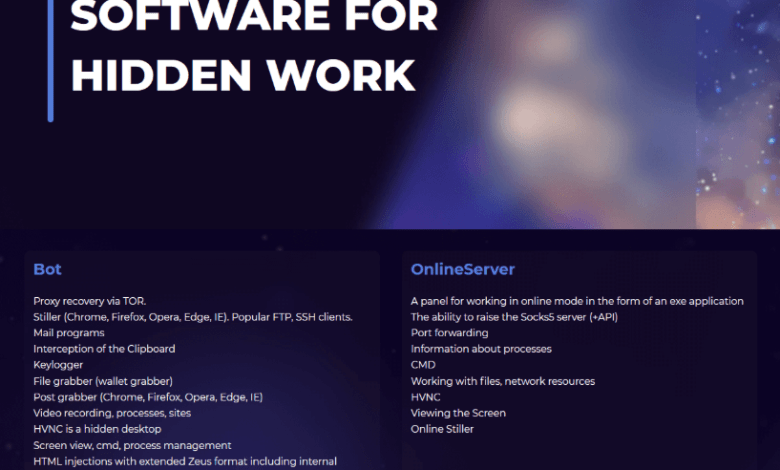
Danabot’s feature, promoted on its support website. Image: welivesecurity.com.
Originally discovered by researchers at Email Security in May 2018 Proof pointDanabot is a malware service platform specializing in certificate theft and bank fraud.
today, U.S. Department of Justice The UN has filed criminal lawsuits and indictments starting in 2022, which alleges that the FBI has identified at least 40 branches that pay between $3,000 and $4,000 a month to access the information thief platform.
The government said the malware infected more than 300,000 systems worldwide, with an estimated loss of more than $50 million. The leader of Danabot’s conspiracy is known as Aleksandr Stepanov39, also known as “Jimby,” and Artem Aleksandrovich Kalinkin34, also known as “onix”, Novosibirsk, Russia. Kalinkin is an IT engineer at the Russian state-owned energy giant Gazpromise. His Facebook profile is named “Maffiozi”.
According to the FBI, there are at least two major versions of the Dash Knife. The first was sold between 2018 and June 2020, when malware was stopped on the Russian cybercrime forum. The government claims that the second edition of Danabot (appeared in January 2021) was provided to co-conspirators for military, diplomatic and non-governmental computers targeting multiple countries, including the United States, Belarus, Britain, Germany, Germany and Russia.
The grand jury indictment on September 20, 2022 said: “Unguided accomplices will use spy variants to compromise global computers and steal sensitive diplomatic communication, certificates and other data.
The indictment says the FBI, which Danabot authors used to control its malware, caught the server in 2022, as well as the servers that store stolen victim data. The government said the server data also showed many instances in which Danabot defendants infected his PC, uploading their credentials data to the stolen data repository that Feds caught.
“In some cases, this self-infection seems to be done intentionally in order to test, analyze or improve malware,” the criminal complaint reads. “In other cases, infection seems to be unintentional – one of the dangers of committing cybercrime is that criminals sometimes mistakenly infect their own malware.”
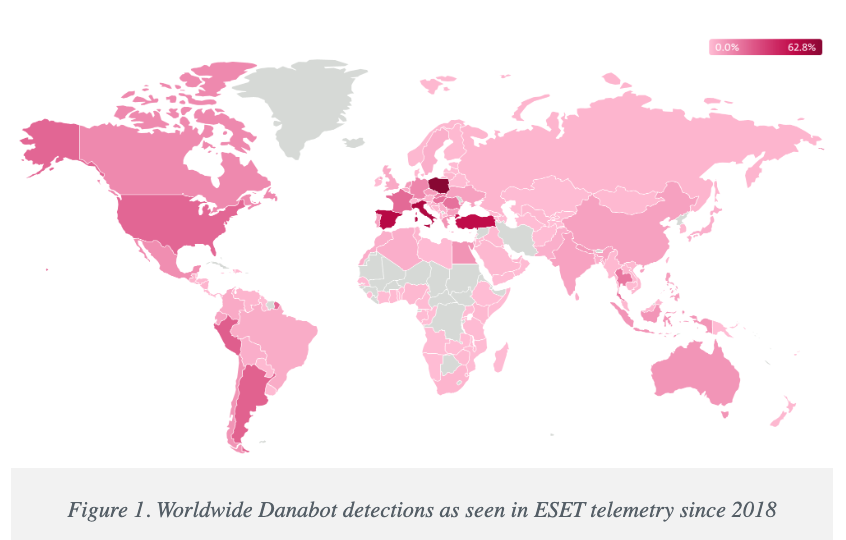
Image: welivesecurity.com
A statement from the Justice Department said that as part of today’s action, National Defense Criminal Investigation Services (DCIS) occupied Danabot control servers, including dozens of virtual servers hosted in the United States. The government said it is now working with industry partners to notify Danabot victims and help remediate the infection. The statement attributes many security companies to providing assistance to the government, including eset,,,,, Flash point,,,,, Google,,,,, Intel 471,,,,, lumen,,,,, PayPal,,,,, Proof point,,,,, Cyrmu Teamand ZScaler.
Financially oriented malware that has been repurposed for espionage is not unheard of. A variant Zeus TrojanBetween 2007 and 2015, used in numerous online banking attacks on U.S. and European companies, a period of time its authors moved to spy missions.
As detailed in this 2015 story, the author of Zeus trojan created a custom version of malware used purely as a spy machine that searched Ukraine for infected systems to obtain specific keywords in emails and documents that may only be found in classified documents.
16 Danabot defendants’ public charges are the second day Microsoft Joining a range of tech companies, Lumma Stealer, the IT infrastructure of another malware service, also ranges from $250 to $1,000 a month in a tiered subscription. Additionally, Microsoft filed a civil lawsuit to seize control of the 2,300 domain names used by Lumma stealers and their branches.
Further reading:
Danabot: Analyzing a fallen empire
ZScaler Blog: Danabot launches DDOS attack against Ukrainian Ministry of Defense
FlashPoint: Operation of the final game Danabot malware
March 2022 Criminal Complaints Artem Aleksandrovich Kalinkin
16 defendants named in September 2022



