Bitcoin Mempool: Relay Network Dynamics

In the previous MEMPOOL article, I covered different kinds of relay strategy filters, why they exist and how each type of filter prevents the incentives that confirm different types of transactions. In this article, I will look at the dynamics of the relay network when some nodes on the network are running different relay strategies compared to other nodes.
All others are equal, and when nodes on the network run homogeneous relay strategies in their Mumbai Islands, all transactions should spread throughout the network as they pay the smallest fees during the large transaction back savings. Things change when different nodes on the network run heterogeneous policies.
The Bitcoin relay network operates with the best efforts using the so-called flood fill architecture. This means that when a node receives a transaction, it forwards to other nodes, except from the node that received the transaction, it is connected to. This is an efficient network architecture, but in the context of a decentralized system it provides a high guarantee that transactions will eventually reach their intended destination, i.e. miners.
Filters are introduced in the node’s relay strategy to limit the propagation of friction in the theory of relays that originally valid transactions introduce friction to the transaction and reduce the reliability of the network’s ability to perform this function. In fact, things are not that simple.
How much friction prevents propagation
Let’s take a look at a simplified example of the composition of different network nodes. In the following figure, the blue node represents Will be Propagate some consensus valid transactions of any category, and the red node represents no Spread these transactions. Collective miners said in the center that it is a simple representation that the transaction users ultimately want their transaction to end to be confirmed in the blockchain.
This is a model of the network where nodes refuse to propagate these transactions is a significant minority. As you can clearly see, any node on the network that accepts them has a clear way to communicate it to miners. The two nodes trying to limit the spread of transactions throughout the network have no effect on the final receipt of the miner node.
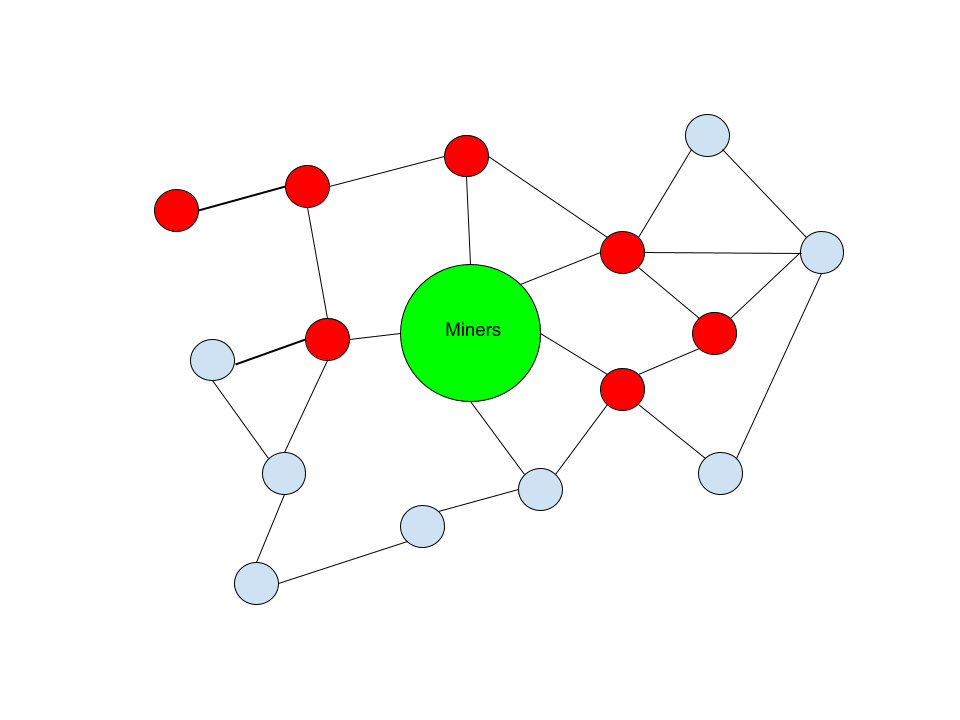
In this figure, you can see that almost half of the sample network is developing a filtering strategy for this type of transaction. Nevertheless, only a part of the network that spreads these transactions is cut off from the miners’ road. The remaining nodes that are not filtered still have clear paths to the miner. This has introduced a certain degree of friction for some users, but others are still free to participate in the spread of these transactions.
Even for users affected by filtering nodes, only a single connection to a network node that has not been cut off from the miner (or a direct connection to the miner) is required in order to remove this friction. If the real relay network has a similar composition to this example, it needs to take a single new connection to alleviate the problem.
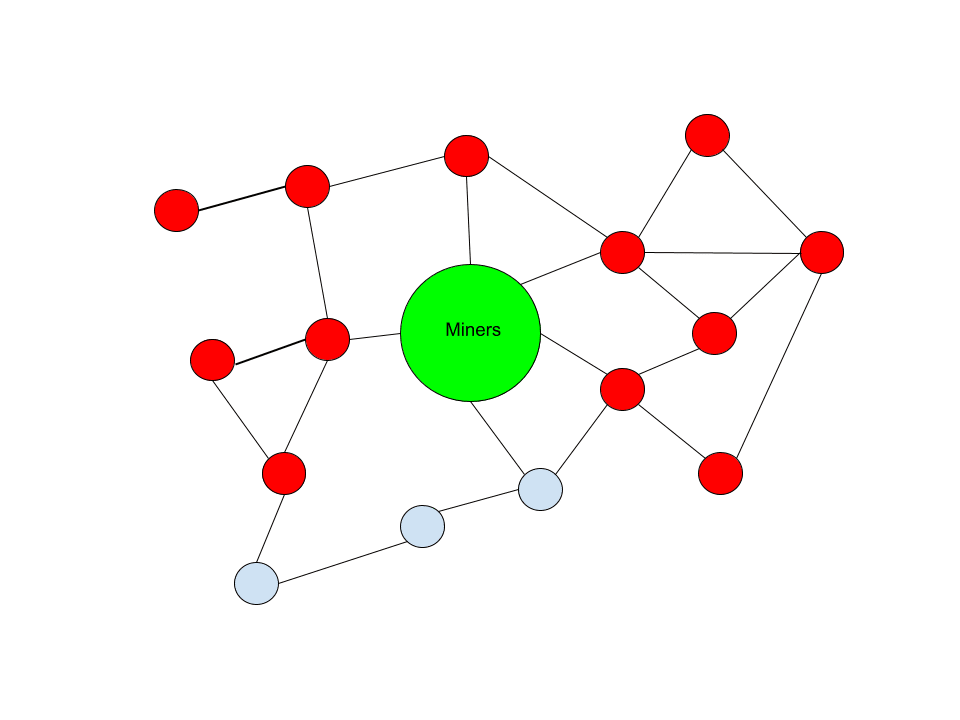
In this case, only a small percentage of the network is actually spreading these transactions. The rest of the network is undergoing filtering policies to prevent it from spreading. But even in this case, those nodes that are not filtered still have a clear way to propagate them to miners.
To ensure they eventually spread to miners, only a few non-filtered nodes are necessary. Priority peer logic, i.e. functionality, to ensure your node prefers peers that implement the same software version or relay policy. These types of solutions guarantee that peers who will spread something to others won’t find each other and stay in touch throughout the network.
A tolerant minority
As you can see, even in the face of the vast majority of examples of the vast majority of public networks, they engage in filtering a specific category of transactions, and everything they need to successfully spread to miners throughout the network is the network that few networks spread and relay them.
These nodes will essentially create a “subnet” in a larger public relay network through any technical mechanism to ensure there is a viable path from engaging in these types of transactions to users who are willing to include them in their neighborhoods.
Basically, there is nothing to do with the Sybil attack except for SYBIL attacks on all of these nodes, Sybil attacks require only one honest connection to be completely defeated, so there is nothing to do. Similarly, an honest node establishing a large connection with other nodes on the network can make the cost of Sybil attacks expensive. The more connections it creates, the more Sybil nodes it has to rotate to consume all its connection slots.
What if there are no few?
So, what if there is no tolerance of ethnic minorities? What happens to such a transaction in this case?
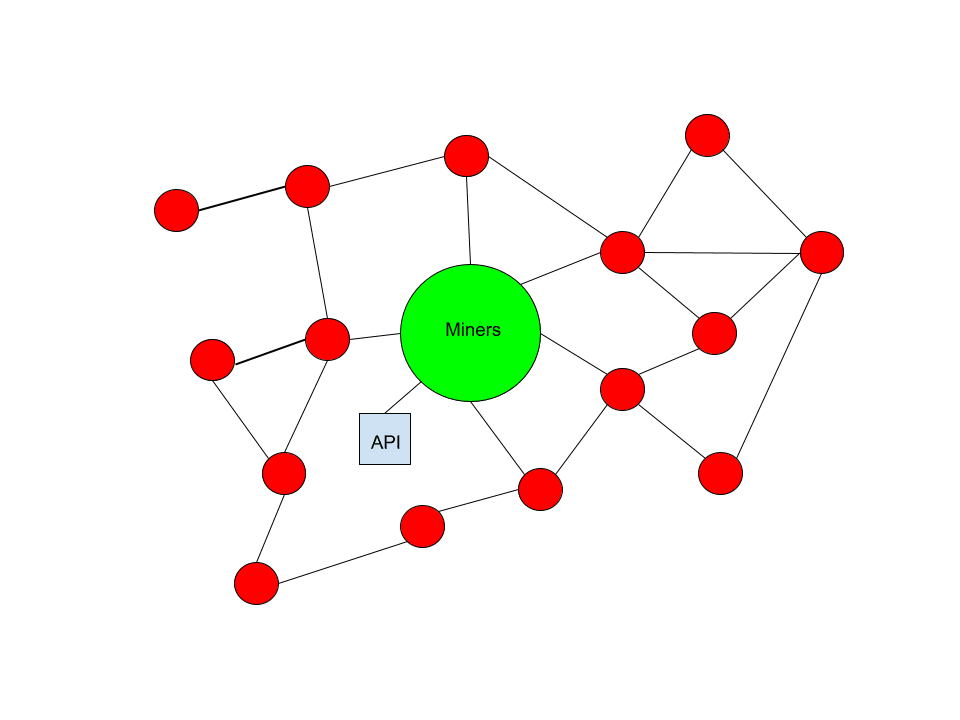
If the user still wants to make them and pay the miners, they will be confirmed. The miner will simply set up an API. The role of miners is to confirm transactions, and the reason is to maximize profits. Miners are not selfless entities, nor are they morally or ideologically motivated, they are a business. They exist to make money.
If the user is willing to pay for some type of transaction and the entire public relay network refuses to spread these transactions to the miners to include them in the block, the miner will create another way for the user to submit these transactions to them.
When a customer exists, as a profit-motivated actor, it is just a reasonable move to hope to pay you.
Relay policy is not a replacement consensus
Ultimately, relay policies are not able to successfully review transactions, users are willing to pay for them, and miners do not have some incredible situations to deny users willing to pay (such as material damage to nodes on the network or material damage to nodes on the network or damage to network, i.e. crashed nodes to sell barriers to validate hours to verify consumption pcs, etc.
If it is indeed considered undesirable by Bitcoin users and node operators, there is no solution to prevent them from confirming in a blockchain where there is no consensus change to invalidate it.
If transactions can be simply prevented from being confirmed by policies implemented on the relay network, then Bitcoin will not be check-resistant.



