Doge siphoned NLRB case data – security

Have a security architect National Labor and Industrial Relations Commission (NLRB) The charges come from Elon Musk‘ Ministry of Government Efficiency (DOGE) Transfers gigabytes of sensitive data from the agency case files using a configured short-life account to transfer almost no trace of network activity. The unusual big data outflow coincides with multiple login attempts at Russian Internet addresses that attempt to use valid credentials for newly created Doge user accounts, the NLRB whistleblower said.
The cover letter from the Bellus whistleblower’s statement was sent to the leaders of the Senate Intelligence Committee.
The allegations were in a letter to the Senate Intelligence Choice Committee on April 14. Daniel J. Berulisa 38-year-old security architect located in NLRB.
NPRThis is the first person to report a complaint from the Bellus whistleblower, who said the NLRB is a small independent federal agency that investigates and rules complaints about unfair labor practices and stores “the proceeds of potentially sensitive data from confidential information from employees who want to form unions that they want to form unions to proprietary business information.”
The complaint documents will last for a month starting on March 3, during which time, it is reported that in the NLRB system, an all-round “tenant management” account is required to be created, which should be exempted from network recording activity, or detailed records of all actions taken by these accounts will be kept.
Bellus said the new Doge account has unlimited permission to read, copy and change the information contained in the NLRB database. New accounts can also limit log visibility, delay retention, route logs, and even delete them altogether – top user privileges that neither Bellus nor his bosses do.
On March 3, a black SUV accompanied police to escort to his building – NLRB headquarters in Washington, D.C., and DOGE employees did not talk to Berulis or anyone else in NLRB IT staff, but met with leaders of the agency.
“Our agent CIO tells us not to comply with the standard operating procedures with the creation of Doge accounts and there is no log or record for accounts created by Doge employees, they require the highest access.”
“We have built roles that auditors can use and widely used in the past, but have no ability to make changes or access subsystems without approval,” he continued. “Their suggestions for using these accounts are not open to discussion.”
Berulis found that on March 3, one of the threshold accounts created an opaque virtual environment called a “container” that can be used to build and run programs or scripts without revealing its activities to the rest of the world. Bellus said the container caught his attention because he investigated his colleagues and found that none of them used containers in the NLRB network.
Bellus said he also noticed a significant increase in the agency’s upcoming traffic early the next morning – between about 3 a.m. on Tuesday, March 4 and 4 a.m. ET. He said a few days of investigation with colleagues confirmed that one of the new accounts had transferred about 10 GB of data from NLRB nxgen Case management system.
Neither he nor his colleagues have the necessary network access to review which files are touched or transferred, or even where they go. But his complaint states that the NXGEN database contains sensitive information about unions, ongoing legal cases and company secrets.
“I also don’t know if the total number of data is only 10GB, or whether it’s before merge and compress,” Bellulis told the Senator. “This opens up the possibility that more data will be eliminated. In any case, this kind of spike is extremely rare because the data almost never leaves the NLRB database directly.”
Bellus said he and his colleagues became even more shocked when they discovered nearly twenty-two login attempts from Russian internet addresses (83.149.30,186), which provided valid login credentials for the Doge Employee account-created just minutes ago. Bellus said these attempts were blocked due to rules prohibiting login from non-U.S. locations.
“The people who attempted to log in were using one of the newly created accounts used in other Doge-related activities and stopped them due to the authentication flow just because we don’t have the country’s login policy activation, so it seems they have the correct username and password,” Berulis wrote. “There are more than 20 such attempts, and it is particularly worrying that many of these login attempts happened within 15 minutes of accounts created by Doge engineers.”
According to Berulis, a named structure of a Microsoft user account is connected to suspicious activity, suggesting it was created and removed from NLRB’s cloud system for Doge: “”[email protected]. “He also discovered other new Microsoft Cloud Administrator accounts with non-standard usernames, including “Whitesox, Chicago M.” and”Jamaican Ballroom R.. ”
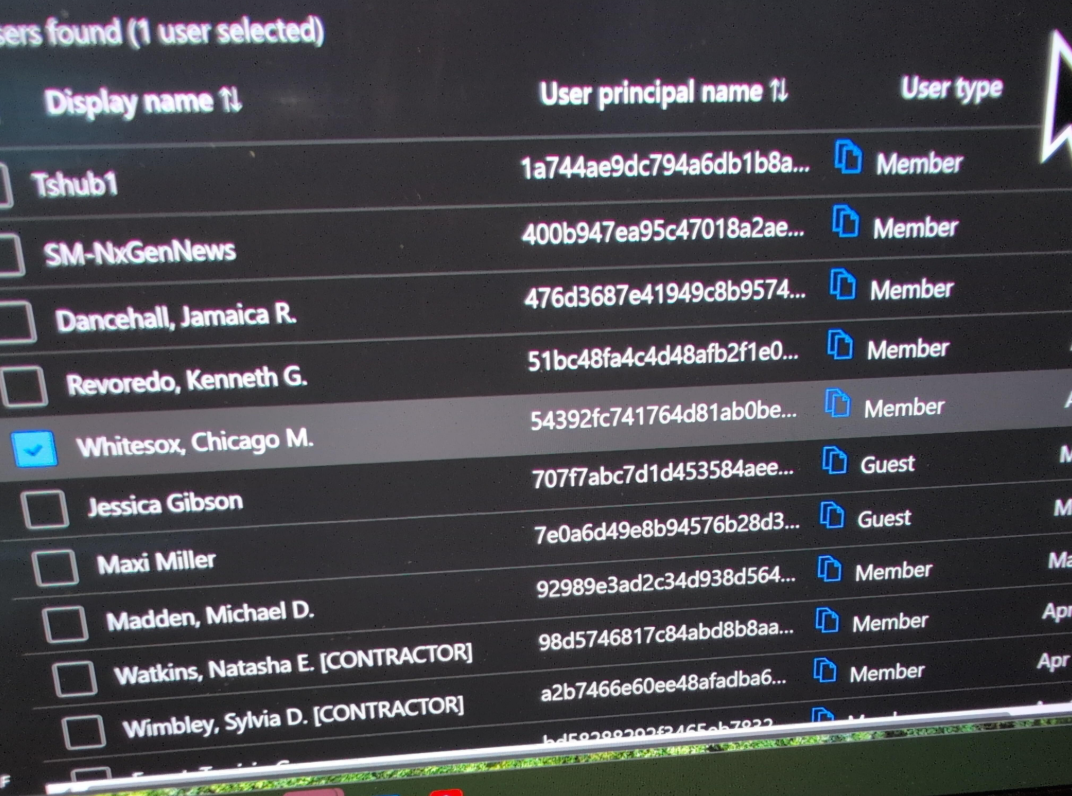
Screenshots shared by Berulis show suspicious user accounts.
On March 5, Berulis recorded a large number of logs of recently created network resources Microsoft Azure is set to “off”, which means it no longer collects and records data like it should have.
Bellus said he found out that someone downloaded three external code libraries from it github Neither NLRB nor its contractors have used it. A “readme” file in a code bundle explains that it was created for rotational connections through a large number of cloud internet addresses that “used as a proxy for generating IPSs within pseudo-in-one” for network scratches and brute force.” Brute force attacks involve automatic login attempts, trying many credential combinations in a fast sequence.
The complaint says that by March 17, NLRB no longer needs to fully investigate the resources or network access required for odd activities of Doge accounts, and the agency’s deputy chief information officer has agreed that the issue should be reported to USA. Operated by the Department of Homeland Security Cybersecurity and Infrastructure Security Agency (CISA), US-CERT provides on-site cyber incident response capabilities to federal and state agencies.
But Bellus said that between April 3 and 4, he and his colleagues’ CIO were told: “Instructions lowered the core U.S. reports and investigations, and we were instructed not to move forward or make official reports.” Bellus said it was he who decided to make his discovery public.
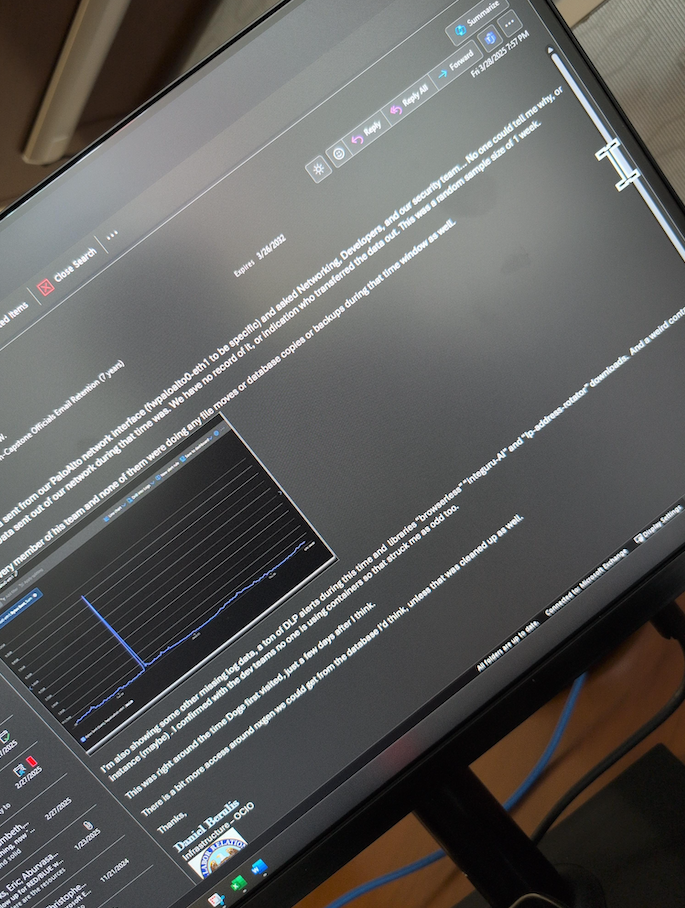
An email to his colleagues dated March 28, Daniel Berulis references unexplained traffic spikes earlier this month, as well as unauthorized user account security control changes.
Tim BeareseNLRB’s acting press secretary told NPR that Doge had neither requested nor received access to its system, and that “the agency investigated after Berulis raised his concerns, but was determined that no violation of the proxy system occurred.” NLRB did not respond to Krebssecurity’s questions.
Nevertheless, Berulis shared many support screenshots to show proxy email discussions about unexplained account activity for Doge account attribution, as well as Microsoft’s NLRB security alerts regarding observed network exceptions over the described timeframe.
As CNN Last month, NLRB has been reported President Trump Three board members were fired so that the agency had no quorum to run.
“Despite limitations, the agency has become harsh and harsh around some of the richest and most powerful people in the United States, especially Trump’s main supporter Elon Musk is economically and politically arguably.”
Both Amazon With Musk SpaceX The NLRB has been suing the agency for complaints filed against the workers’ rights and disputes between trade union organizations, believing that the existence of the NLRB is unconstitutional. On March 5, the U.S. Court of Appeal unanimously rejected Musk’s claim that the structure of the NLRB was somehow contrary to the Constitution.
Berulis shared screenshots with Krebsonsecurity, showing that NPR posted a story about his claims (April 14), and NLRB’s agent CIO sent an email stating that administrative controls had been removed from all employee accounts. This means that the agency’s IT staff suddenly fail to get the job done correctly, Bellus said.
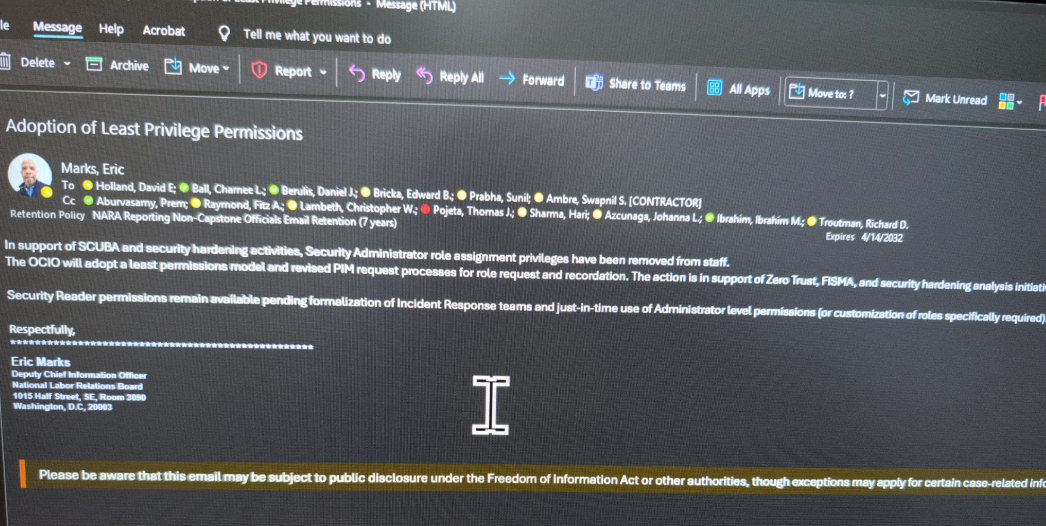
Emailed by Eric Marks, deputy chief information officer of NLRB, notifying employees of the security administrator privileges.
Berulis shares an agency-wide screenshot on April 16 by NLRB Directors Rashan Hamilton Said Doge officials requested a meeting and reiterated that the agency has no claim that there is no “formal” connection with any Doge personnel. The news told NLRB employees that two Doge deputies will give part-time details on how many months.

NLRB director Lasharn Hamilton posted an email on April 16 that pointed out that the agency had not previously contacted Doge personnel.
Berulis told Krebsonsecurity that he is submitting a support ticket to Microsoft to request more information about the Doge account when its network administrator access is restricted. Now, he hopes lawmakers ask Microsoft to provide more information about what’s really going on with the account.
“That will make us more insightful,” he said. “Microsoft has to be able to see pictures better than we do. Anyway, that’s my goal.”
Bellus’ lawyer told lawmakers that on April 7, when his client and legal team were preparing to file a complaint by whistleblower, someone photographed Mr Bellus’s home with a drone and someone posted a threatening note as he walked near him.
“The threat statement clearly refers to this disclosure he has prepared for you as the appropriate supervisory authority,” said Bellus’s attorney. Andrew P. Bakaj. “While we don’t know who did this, we can only speculate that it involves people with the ability to access NLRB systems.”
Bellus said that the responses from friends, colleagues and even the public were largely supported and he did not regret standing up.
“I didn’t expect the letter from the door or [agency] Leader,” he said. “If I had to do this, would I do it again? Yes, because this is not even the first time that it is a real choice. ”
Currently, Mr. Berulis is dismissed in NLRB. This is also true, he said, given that he was deprived of the tools he needed to do his job at an agency.
“They came in and accepted full administrative control and locked everyone in, and said they would allocate limited permissions on the basis of need,” Bellulis said. “We really did nothing, so we were actually calculating the rewards for the ceiling tiles.”
Further reading: Berulis’s Complaint (PDF).



