Feeded by fake verification codes in a dark Adtech empire – Krebs

Late last year, security researchers made a shocking discovery: Kremlin-backed disinformation campaigns powered the vast ecosystem of online grocery stores and website hackers by leveraging the same malicious advertising technology to bypass temperance on social media platforms. A new report on the consequences of the survey found that the dark ad tech industry is more resilient and incest than previously known.
Image: Infoblox.
November 2024, Researchers at Security Company Quran A survey of “Doppelganger” was published, which promotes pro-Russian narratives and penetrates European media landscape by promoting fake news through the network of cloned websites.
The Doppelganger campaign uses dedicated links to bounce visitors’ browsers through a series of domain names before providing fake news content. Qurium found Doppelganger relied on a sophisticated “domain masking” service that allows websites to show different content to search engines than regular visitors. The use of masking services helps disinformation sites to be online longer than before, while ensuring that only the target audience can view the expected content.
Qurium found that Doppelganger’s shawl service also facilitated online dating sites, and Vextrioconsidered to be the oldest malicious traffic distribution system (TDS) in existence. While legitimate advertising networks typically use TDS to manage traffic from different sources and track content or content behind each click, Vextrio’s TDS mainly manages network traffic for victims of phishing, malware and social engineering scams.
breaking Bad
Qurium digs deeper into Doppelganger’s shawl service, using Swiss internet providers as the first entry point in the domain redirection chain. They also noticed that the same infrastructure hosted a pair of shared-branded membership marketing services that attracted traffic to adult dating sites: Lospollos[.]com and tacoloco[.]company.
The Lospollos Advertising Network combines many elements and references from the popular HBO series “Breaking Bad”, reflecting the fictional “Los Pollos Hermanos” restaurant chain, a money laundering campaign by violent methamphetamine cartels.

The lospollos ad network calls on the roles and themes of the popular show Breaking Bad. The LOSPOLLOS logo (top left) is an image of Gustavo Fring, owner of the fictional chicken restaurant chain in the show.
Members who signed with Lospollos were given JavaScript’s heavy “”Smart links“Bring traffic to Vextrio TD, which in turn distributes traffic among various advertising partners, including dating services, sweepstakes offerings, bait and switch mobile apps, financial scams and malware download sites.
Lospollos branches usually stitch these smart links to WordPress Through websites where a known vulnerability is hacked, these branches receive a small commission every time an internet user is referred to one of these baits by any of their hacking sites.
The Los Pollos Advertising Network promotes itself on LinkedIn.
According to Qurium, Tacoloco is a monetized transportation network that uses deceptive strategies to lure Internet users to enable “push notifications”, a cross-platform browser standard that allows websites to display pop-up messages displayed outside the browser. For example, on Microsoft Windows systems, these notifications are usually displayed in the lower right corner of the screen – above the system clock.
As far as Vextrio and Tacoloco are concerned, notification approval requests are both deceptive – disguised as a “Captcha” challenge designed to distinguish between automated bot traffic and real visitors. Over the years, Vextrio and its partners have successfully tricked countless users into enabling these website notifications and then used them to continually use various Phony virus alerts and misleading pop-up messages to continuously satisfy the victim’s devices.
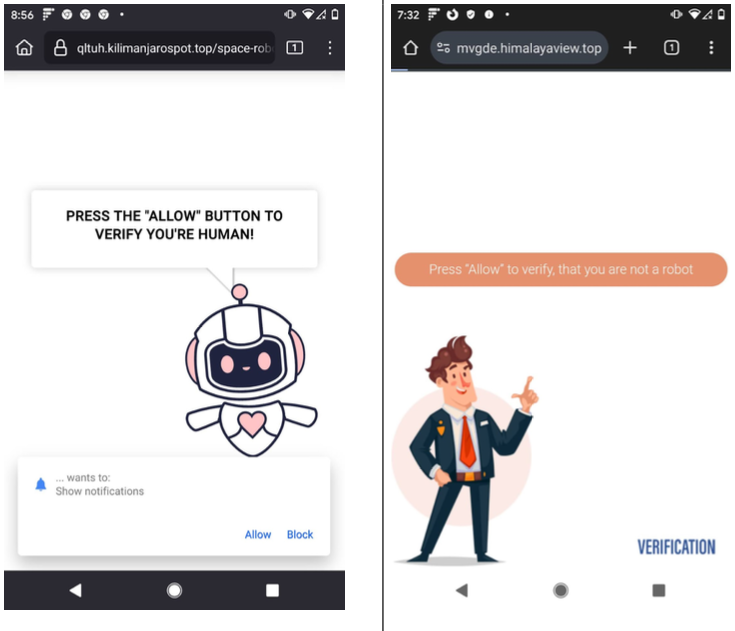
An example of a vextrio landing page causing the user to accept push notifications on their device.
According to the December 2024 annual report Godaddy,,,,, Nearly 40% of visitors redirected via Lospollos SmartLinks in 2024 are redirected to Vextrio.
ADSPRO and TEKNOLOGY
On November 14, 2024, Qurium published a study to support its discovery Lospollos and Tacoloco are service-operated discovery ADSPRO Groupa company registered in the Czech Republic and Russia, which operates its infrastructure in the Swiss hosting provider’s infrastructure C41 and Teknology SA.
Qurium noted that Lospollos and Tacoloco sites indicate that their content is copyrighted Bytecore AG and Skyforge Digital AGthese two Swiss companies run by Teknology SA owners, Guilio Vitorrio Leonardo Cerutti. Further investigations show that Lospollos and Tacoloco were developed by a company called Holacodelisted Cerutti as CEO.
The apps sold by HolaCode include many VPN services, as well as one called Garbage crocodile This claims to stop unnecessary push notifications. But in January, Infoblox said they tested the app on their mobile device and found it hidden the user’s notifications, then stopped hiding and asked for payments 24 hours later. Spamshield then changed its developer name from Holacode to aplabzalthough InfoBlox notes, several terms of service that reshape the Aplabz app still references Holacode in its terms of service.
Incredibly, Cerutti threatened to sue me for defamation, even before I spoke his name or asked him to comment (Cerutti sent it to an unsolicited legal threat after his company and my name tagged an Infoblox post about Vextrio only in the Infoblox post on LinkedIn).
When asked to comment on the discovery of the Quran and Infoblox, Cerutti strongly denied it was related to Vextrio. Cerutti asserted that his companies strictly comply with the regulations of the country they operate and are completely transparent about all businesses.
“We are a team that operates in the advertising and marketing field and plans through the member network.” “I’m not [going] To say we are perfect, but I strongly claim that we have no connection to Vextrio at all. ”
“Unfortunately, as large players in this space, we can also handle a lot of publisher fraud, rough traffic, fake clicks, bots, hacks, listing and reselling publisher accounts, etc.,” Cerutti continued. “We bleed a lot of money for such malfeasance and have regular internal screening and reviews in constant battles to eliminate bad traffic sources. It’s also a competitive space where some upstarts often play a dirty role in more mature mainstream players like us.”
Researchers at Security Company collaborate with Qurium infoblox Detailed information about Vextrio infrastructure has been released to its industry partners. Just four days after Qurium released its discovery, Lospollos announced that it was suspending its monetization services. Less than a month later, Adspro was renamed Targeting the world.
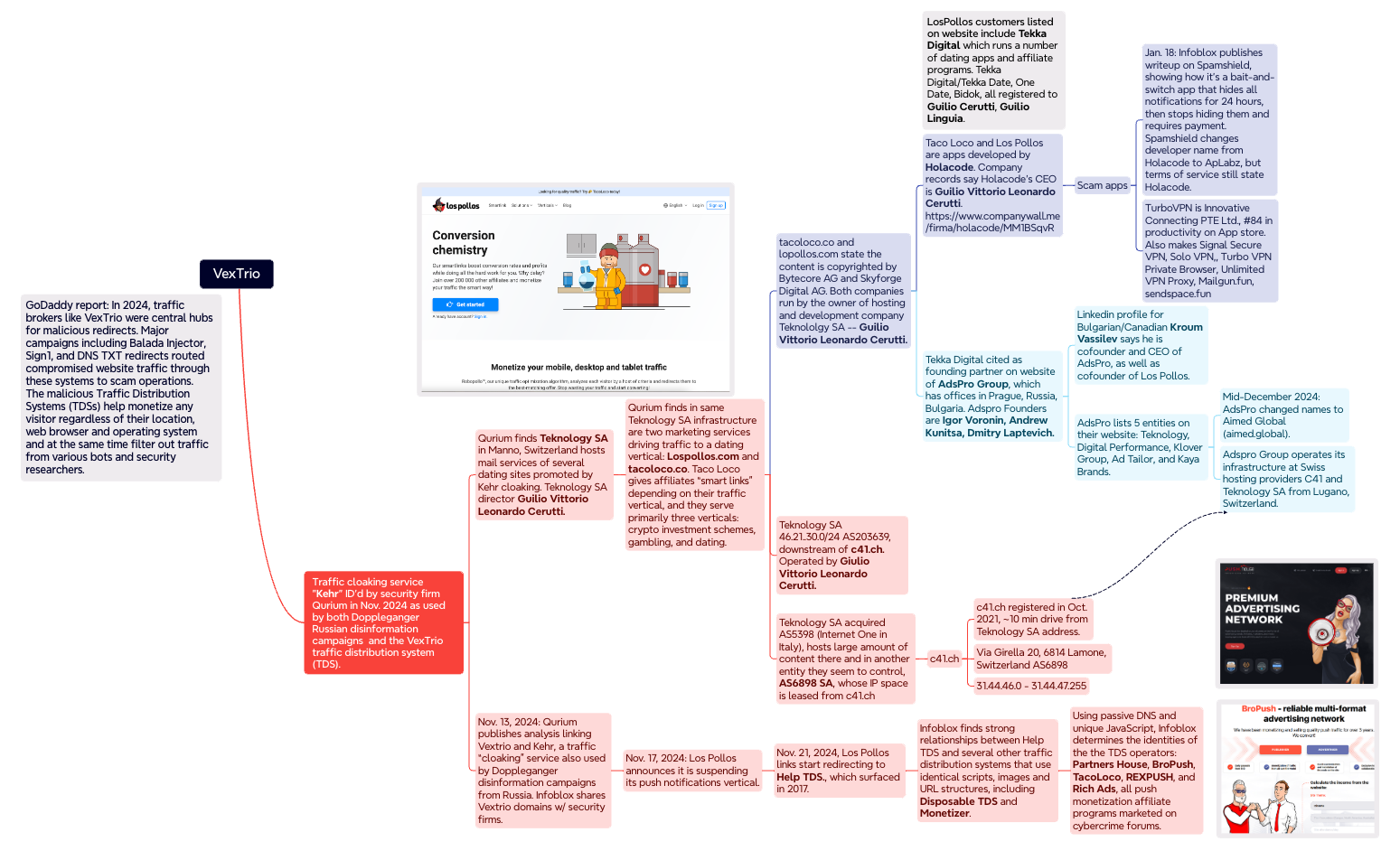
A mind map illustrates some of the key findings and connections in the Infoblox and Qurium surveys. Click to zoom in.
A revealing pivot
In March 2025, Godaddy researchers documented how Dollyway – Malware pressure that has been redirecting victims to Vextrio throughout eight years of activity – suddenly stopped doing so on November 20, 2024. Almost overnight, Dollyway and several other malware families who had previously used Vextrio began to drive their traffic through another TD Help TD.
InfoBlox further examines the historical DNS records used by Help TDS and the unique code scripts used, confirming that it has long established exclusive relationships with Vextrio (at least until Lospollos ended in November that pushed for monetization services).
Infoblox said in a report released today that it conducted a detailed analysis of JavaScript code, website bait, smartlinks and DNS patterns and helped TDS connect them with at least four other TDS operators (not counting Tacoloco). These four entities – Partner Home,,,,, Bropush,,,,, Richie and rexpush – All Russia-based monetization programs that pay to drive registration of various programs, but mainly online dating services.
“As Los Pollos pushes monetization toward the end, we have seen a rise in fake verification codes, which can drive users to accept push notifications, especially in partner homes,” the InfoBlox report read. “The relationships of these commercial entities remain a mystery; while they are certainly long-term partners redirecting traffic, and they all have Russian connections, there is no public co-ownership.”
Renee BurtonThe security industry often sees the deceptive approach used by Vextrio and other malicious TDSs as a legally grey area, primarily associated with dangerous security threats such as Adware and Scareware, said Infoblox’s vice president of threat intelligence.
But Burton believes that this view is myopic and helps keep the dark Adtech industry going on, which also drives a large number of direct malware, noting that victims are redirected to Vextrio and vextrio and vextrio-afflio-affliateTDSS every year on websites of hundreds of thousands of victims around the world.
“These TDSs are an evil threat because they are threats you can connect things like information stewards and scams,” Burton said. “From a larger strategic perspective, what I gain is that Russian organized crime controls malicious ADTECH, and these are just some of the many groups.”
What can you do?
As Krebsonsecurity warned back in 2020, it is a good idea to very approve notifications when browsing the web. In many cases, these notifications are benign, but as we have seen, there are many crafty companies that are paying website owners their notification scripts and then reselling them to scammers and online Hucksters’ communication pathways.
If you want to prevent a website from making a notification request, all major browser manufacturers can let you do this – both comprehensively and per website. While it is true that blocking notifications completely can break the functionality of some websites, any device you manage on behalf of a friend or family member who is not very tech-savvy may end up saving everyone a lot.
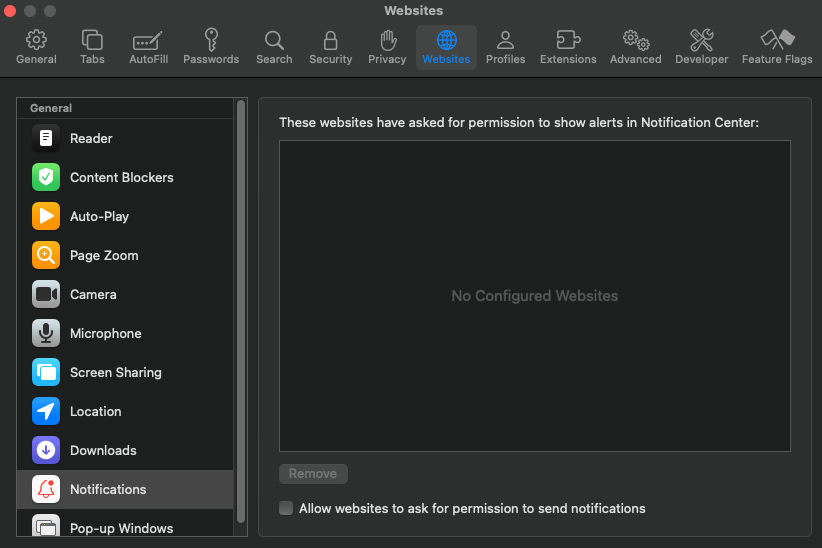
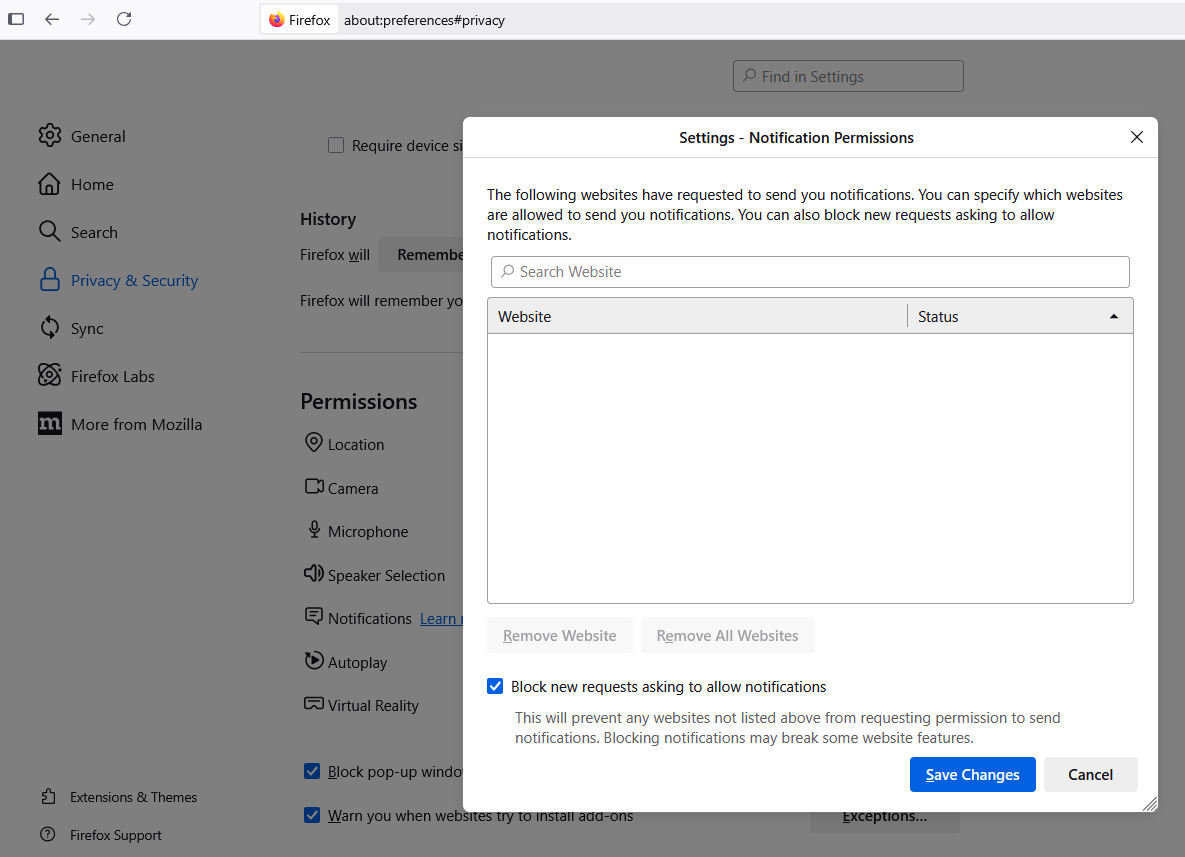
Modify site notification settings Mozilla Firefoxnavigate to Settings, Privacy and Security, Permissions, and click the Settings tab next to Notifications. This page will display any notifications that have been allowed and will allow you to edit or delete any entries. Tick the box next to Block new requests that require permission notifications to be blocked completely.
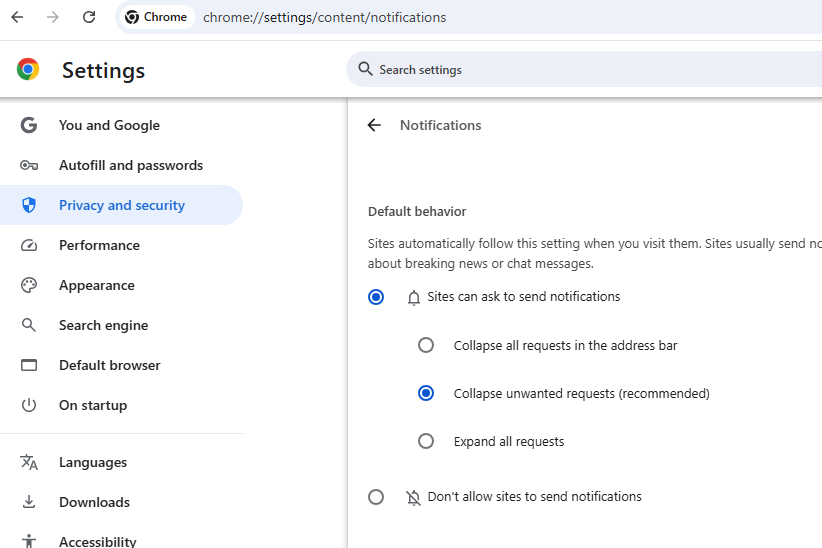
exist Google Chromeclick the icon at the three dots to the right of the address bar and scroll all the way to Settings, Privacy and Security, Site Settings, and Notifications. If you want to eliminate notification requests forever, select the “Don’t allow sites to send notifications” button.
In Apple Safari Browser, go to Settings, Website, and click Notifications in the sidebar. If you want to turn off notification requests completely, uncheck the option “Allow websites to request permission to send notifications”.