Funds for major network vulnerability databases expire

Cybersecurity Professionals Relying on cybersecurity professionals around the world to identify, mitigate and fix security vulnerabilities in software and hardware is potentially compromised. Federally funded nonprofit research and development organization MITER Warned today that its contract maintenance Common vulnerabilities and exposures The (CVE) program (traditionally funded annually by the Department of Homeland Security) will expire on April 16.
A letter from Miter Vice President Yosry Barsoum warned that funds for the CVE program will expire on April 16, 2025.
Thousands of software security flaws are found and reported every year, which are eventually assigned their own unique CVE tracking number (e.g. CVE-2024-43573, which is a Microsoft Windows Redmond’s bug patched last year).
There are hundreds of organizations – called CVE numbering authority (CNA) – Authorized by MITER, these CVE numbers can be granted in newly reported defects. Many of these CNAs are national and government-specific, or related to a single software vendor or vulnerability disclosure platform (also known as the Bug Bounty program).
In short, MITER is a key, widely used resource for centralizing and standardizing information about software vulnerabilities. This means that the information pipeline it provides has been inserted into a range of cybersecurity tools and services that can help organizations identify and patch security holes – ideally before malware or malicious organizations can creep through them.
“What the CVE list really provides is a standardized approach to describing the severity of the defect, and a centralized repository list of which products are defective and need to be updated.” Corelliuma cybersecurity company that sells phone virtualization software used to find security flaws.
In a letter sent to the CVE board today, Miter Vice President Yosry Barsoum Warning that on April 16, 2025, “the current contractual pathway to develop, operate and modernize CVE, as well as several other related plans will expire.”
“In the event of a service outage, we expect CVE to have multiple impacts on CVE, including worsening of national vulnerability databases and consulting, tool providers, incident response operations, and ways of various critical infrastructure,” Barsoum wrote.
Miter told Krebsonsecurity CVE website listing vulnerabilities will continue to increase after funds expire, but new CVE will not be added after April 16.
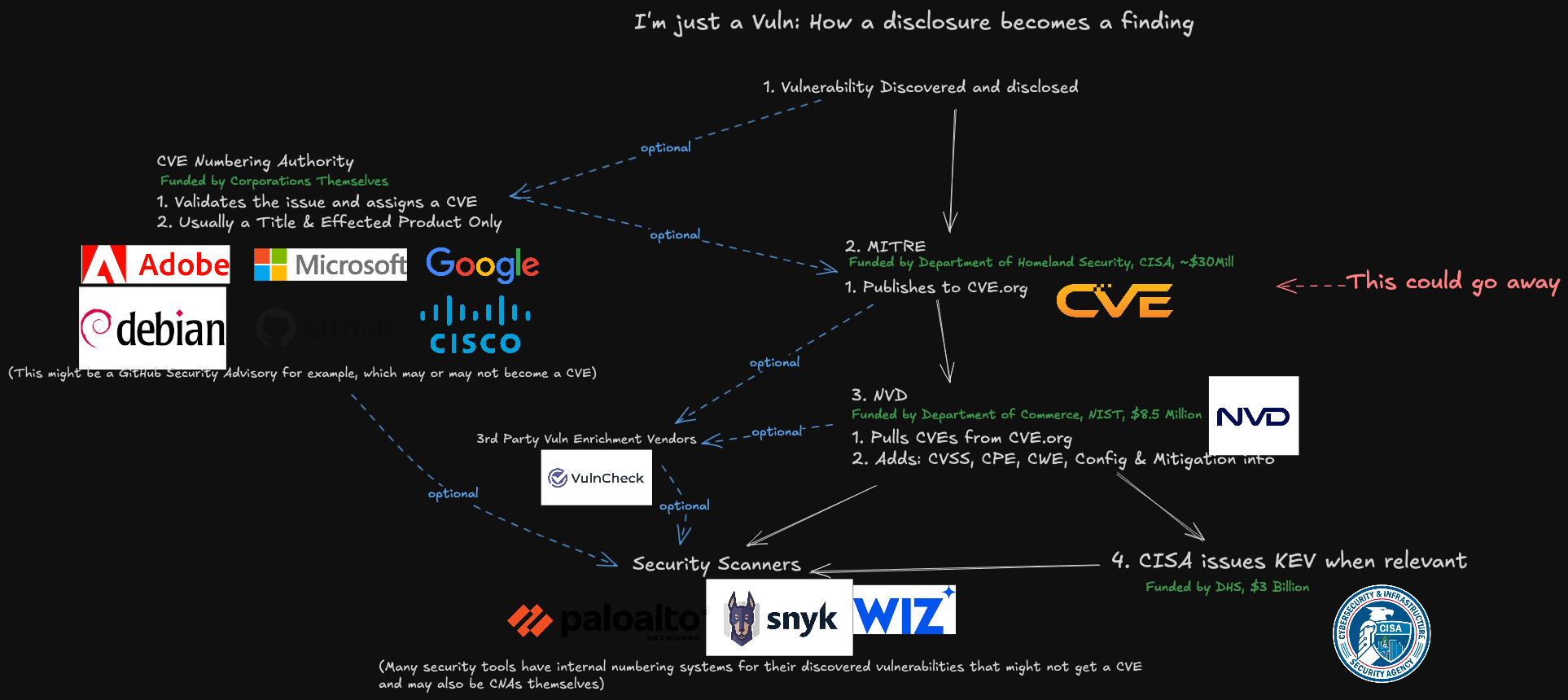
How vulnerability becomes CVE and how it consumes a representation of that information. Image: Latio Tech James Berthoty by LinkedIn.
Department of Homeland Security officials did not immediately respond to a request for comment. The program is through DHS Cybersecurity and Infrastructure Security Bureau (CISA), currently facing budget and staff cuts from the Trump administration. The CVE contract is available on USASPENDEND.GOV, which received a grant of approximately $40 million last year.
Former CISA Director Jen Eastley Saying that the CVE plan is a bit like the Dewey decimal system, but for network security.
“It is the global catalog that helps everyone (security teams, software vendors, researchers, governments) to organize and discuss vulnerability using the same reference system,” Easterly said in an article on LinkedIn. “Without it, everyone is using other catalogs or not at all, no one knows they are talking about the same issue, defenders waste valuable time figuring out what problems, and worst of all, threat actors exploit confusion.”
John Hammondchief security researcher for hosting security companies HunterTell Reuters that when he heard the news that CVE funds were in danger, he swore out loud, and the news of losing the CVE plan was like losing “the language and terminology we used to solve cybersecurity problems.”
“I can’t help but think it’s going to hurt,” Hammond said, who posted YouTube videos to vent the situation and remind others.
Several people close to the matter told Crabson safe that this is not the first time the CVE program’s budget has retained funds by the last minute. Basum’s letter was clearly leaked, sounding promising notes, saying the government is making “a huge effort to continue Mit’s role in supporting the program”.
Without a CVE plan, risk managers within the company will need to constantly monitor many other places for information about new vulnerabilities, which could endanger the security of their IT networks, Tate said. This means that software updates are replaced with errors first, he said, and that software deployed by companies will be deployed longer than before.
“Hopefully they can fix this, but otherwise the list will fail quickly and stop useful,” he said.
Updated, April 16, 11:00 a.m. ET: CVE Board of Directors Announces the Creation of a Nonprofit Organization Today CVE Foundation This will continue the work of the program under the new unspecified funding mechanism and organizational structure.
“Since its inception, the CVE program has been a U.S. government-funded initiative and provides oversight and management under contract,” the press release reads. “While this structure supports the growth of the program, CVE board members have also raised long-term concerns about the sustainability and neutrality of global resources related to individual government sponsors.”
The organization’s website thecvefoundation.org is less than a day old and currently has nothing to do with the exception of a press release foreshadowing its creation. The announcement said the foundation will release more information about its structure and transition plans in the coming days.
Updated, April 16, 4:26 pm: Miter issued a statement today saying, “The incremental funding was identified to make the program work. We appreciate the overwhelming support of these programs expressed by the global network community, industry and government over the past 24 hours. The government continues to work to support the role of MITER in the program and the role of MITER in the program and MITER remains committed to CVE and CVE as global resources.”



