U.S. sanctions cloud provider “funnull” is the primary source of “pig slaughter” scam – Krebs
Image: shutterstock, arthead.
Today, the U.S. government Funnull Technology Inc.a Philippines-based company that provides computer infrastructure for hundreds of thousands of websites involved in virtual currency investment scams, called “Pig slaughter. In January 2025, Krebsonsecurity detailed how to use Funnull as a content delivery network that caters to cybercriminals in search of transportation through cloud providers in the United States.
“Americans lose billions of dollars in these cyber scams every year, and the revenue from these crimes has increased to record levels in 2024.” U.S. Treasury Departmentapproved Funnull and his 40-year-old Chinese administrator Liu Lizhi. “Funnull directly facilitated several of these programs, resulting in more than $200 million in reported losses for U.S. victims.”
The Treasury Department said Funnull’s business is related to most virtual currency investment scam websites reported to the FBI. The agency said Funnull directly facilitated pig slaughterhouses and other programs that caused more than $200 million in American losses.
Pig Butchering is a rampant form of fraud in which people tempting strangers online attract people to invest in fraudulent cryptocurrency trading platforms. The victims were directed to invest more and more money into what seemed to be a very profitable trading platform, only to find that their money disappeared when they hoped to be cashed out.
Scammers often insist that investors pay extra “tax” to their crypto “earnings” before seeing their investment funds again (the disruptor: they never did) and that through these slaughter-type slaughter scams, many shocking people lose six figures or more.
Crabson Security’s January story about Funnull is based on research by security companies Silent pushIt was discovered in October 2024 that a large number of domain names hosted by Funnull are promoting gambling sites that carry logos Nikon Groupa Chinese entity named in the 2024 United Nations Report (PDF) launders millions of dollars in money for the North Korean state-sponsored hacker group Lazarus.
Silent Push discovered that Funnull is a criminal content delivery network (CDN) that comes with a lot of traffic associated with scam websites, converges traffic through a series of dazzling auto-generated domain names and cloud providers in the United States, and then redirects it to malicious or evil sites. The FBI has released a technical writing (PDF) for managing infrastructure for malicious Funnull domains between October 2023 and April 2025.
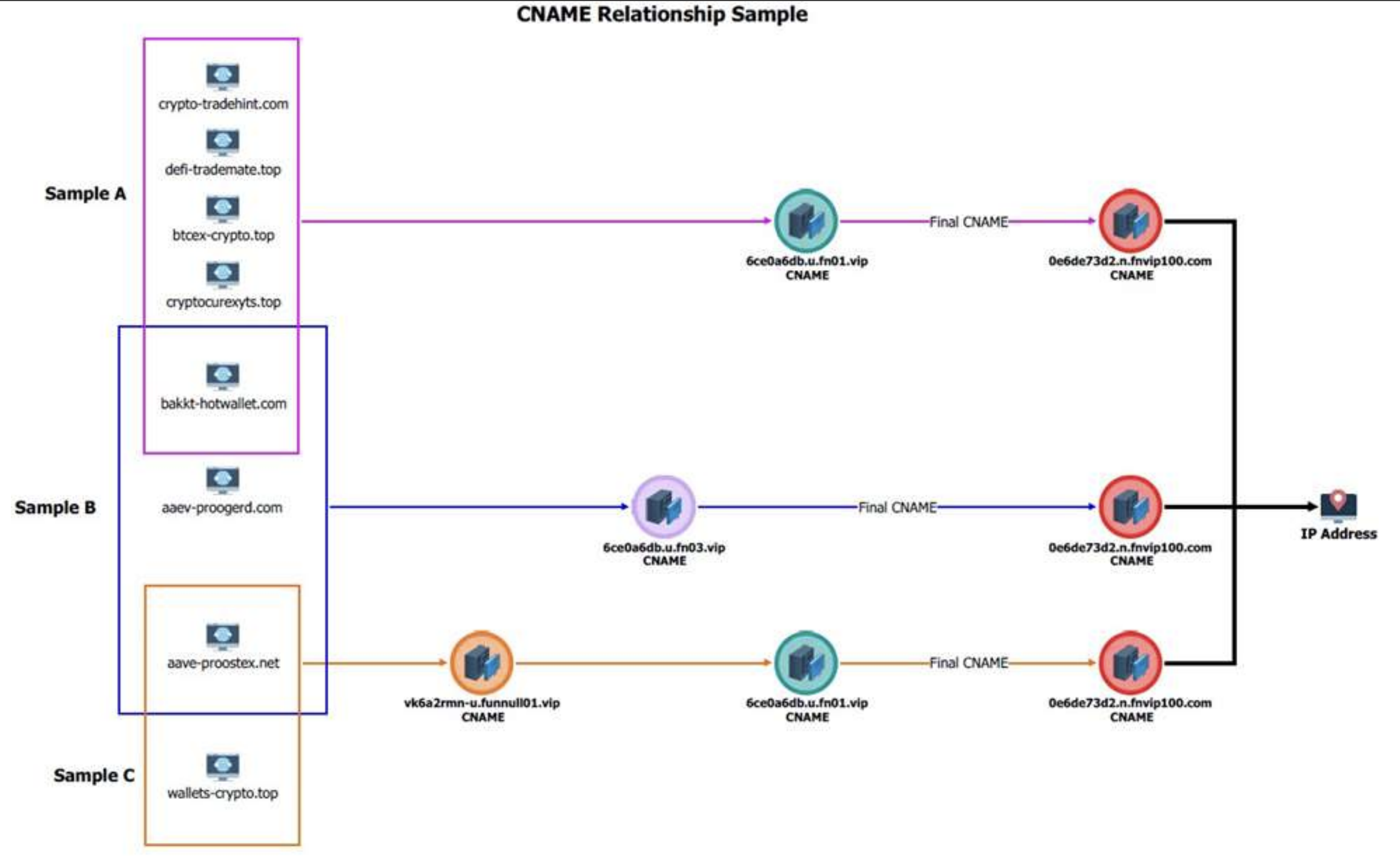
The FBI graph explains how Funnull periodically generates many new domains and maps them to the Internet address of a U.S. cloud provider.
Silent Push revisited Funnull’s infrastructure in January 2025 and found that Funnull is still using many of the same infrastructure Amazon and Microsoft Cloud Internet address was identified as malicious in its October report. After this story Zach Edwards Only one of these companies follows.
Edwards said the silent push no longer sees Microsoft Internet addresses appearing in Funnull’s infrastructure, and Amazon continues to struggle with deleting Funnull servers, including the first one implemented in 2023.
“Amazon is doing a horrible job every day – since they made these claims to you and us in our public blog, they’ve still mapped IPS to Funnull, including some of the time they stayed in inexplicable times,” Edwards said.
Amazon says its Amazon Web Services (AWS) hosting platform is actively fighting back attempts to abuse.
“We have stopped hundreds of attempts related to the group this year and we are looking at the information you shared earlier today,” a statement shared by Amazon read. “If anyone suspects that AWS resources are being used for abuse activities, they can report to AWS Trust & Safetion here using the Report Abuse Table.”
Cloud providers in the United States remain an attractive home base for cybercriminal organizations, as many organizations are not overly aggressive in blocking traffic from U.S.-based cloud networks, as doing so may block access to many legitimate network destinations that are also in the same shared network domain or host.
More importantly, their bad traffic is pooled so that it appears to be coming out of the US cloud internet provider, allowing cybercriminals to connect to the website, from the website address to the geographical proximity (R) to their targets and victims (e.g., your bank’s location-based security control controls).
Funnull isn’t the only cybercrime infrastructure sanctioned this month, a service provider: May 20, 2025, European Union Implement sanctions Stark Industries SolutionsThis is an ISP implemented at the beginning of the Russian invasion of Ukraine and has been used as a global proxy network, obscuring the true source of cyber attacks and disinformation against Russian enemies.
In May 2024, Krebsonsecurity published an in-depth study on Stark Industries Solutions, finding that many malicious traffic across Stark networks such as vulnerability scanning and password brute force attacks are bounced through US-based cloud providers. My reports show that over the years Ivan Neculiti has sold “bullet-proof” hosting services that tell Russian cybercrime forum customers that they will proudly ignore any complaints of abuse or police inquiries.
Stark Industries Solutions home page.
This story examines the history of Stark’s co-founder Moldova brothers Ivan and Yuri Neculitieveryone denies any involvement in cybercrime in the past or currently involved in assisting Russian disinformation or cyberattacks. Despite this, the EU also approved the two brothers.
The EU said Stark and Nikolat brothers “enable a variety of players sponsored and affiliated by Russian states to carry out unstable activities, including coordinated information manipulation and intervention, as well as cyberattacks against trade unions and third countries, to provide these activities designed to hide in European law enforcement and security agencies.”



